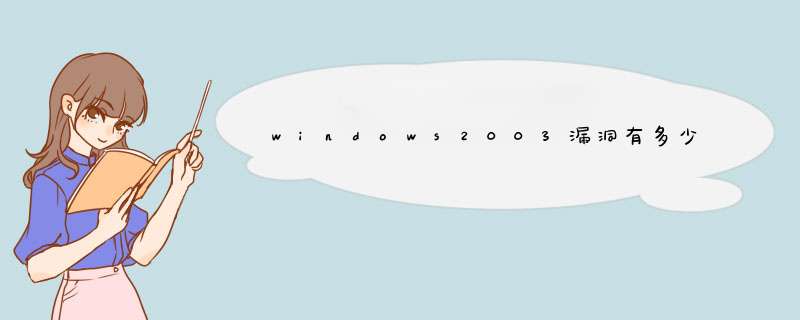
详细资料 + 21.24.0.243 : . 开放
端口列表 : o www (80/tcp) (
发现安全漏洞) o Windows Terminal Services (3389/tcp) (发现
安全提示) o ftp (21/tcp) (发现安全提示) o ms-sql-s (1433/tcp) (发现安全提示) o msrdp (3389/tcp) (发现安全警告) o mssql (1433/tcp) (发现安全提示) . 端口"www (80/tcp)"发现安全漏洞 : The IIS server appears to have the .SHTML ISAPI filter mapped. At least one remote vulnerability has been discovered for the .SHTML filter. This is detailed in Microsoft Advisory MS02-018 and results in a denial of service access to the web server. It is recommended that even if you have patched this vulnerability that you unmap the .SHTML extension, and any other unused ISAPI extensions if they are not required for the operation of your site. An attacker may use this flaw to prevent the remote service from working properly. *** Nessus reports this vulnerability using only *** information that was gathered. Use caution *** when testing without safe checks enabled To unmap the .shtml extension: 1.Open Internet Services Manager. 2.Right-click the Web server choose Properties from the context menu. 3.Master Properties 4.Select WWW Service ->Edit ->HomeDirectory ->Configuration and remove the reference to .shtml/shtm and sht from the list. Risk factor : Medium CVE_ID : CVE-2002-0072 BUGTRAQ_ID : 1066, 4479 NESSUS_ID : 10937 Other references : IAVA:2002-A-00021、为计算机安装最新的安全补丁,微软已发布补丁MS17-010修复了“永恒之蓝”攻击的系统漏洞,请尽快安装此安全补丁;对于windows XP、2003等微软已不再提供安全更新的机器,可使用360“NSA武器库免疫工具”检测系统是否存在漏洞,并关闭受到漏洞影响的端口,可以避免遭到勒索软件等病毒的侵害。
2、关闭445、135、137、138、139端口,关闭网络共享。
3、强化网络安全意识:不明链接不要点击,不明文件不要下载,不明邮件不要打开……
4、尽快(今后定期)备份自己电脑中的重要文件资料到移动硬盘、U盘,备份完后脱机保存该磁盘。
5、建议仍在使用windows xp, windows 2003操作系统的用户尽快升级到 window 7/windows 10,或 windows 2008/2012/2016操作系统。


 微信扫一扫
微信扫一扫
 支付宝扫一扫
支付宝扫一扫
评论列表(0条)